Project Background
The Harbin No.5 Hospital was founded in 1955 with an area of 50,000 square meters and a built-up area of 37,000 square meters. Fifty years after it was established, the hospital developed into a Third-Grade First-Class hospital integrating medical treatment, scientific research and teaching, with orthopedics and the burn department as provincial key specialties. The hospital was listed by the Ministry of Health People’s Republic of China as a National Emergency Rescue Center Network Hospital. With increasing dependence of health services on information systems, the informatization environment gradually deteriorated, and security issues became more prominent. Under these circumstances, several medical and health institutions started paying attention to information security, and efforts in this respect are progressing gradually.
In the Guiding Opinions on Information Security Classification Protection in Health Industry (WBF [2011] No. 85), it is pointed out that in accordance with the Classification Protection System for National Information Security and following the relevant standards and norms, it is necessary to conduct comprehensive graded protection for information security, system construction rectification and graded evaluation in the health industry. It requires the definition of key points of information security, implementation of information security responsibilities, establishment of a long-term mechanism of graded protection for information security, and effective improvement in information security protection, danger detection and emergency response in the health industry. Doing a good job in the information security classification protection is of immense importance in promoting healthy development of health informatization, guarantee reforms in the medical and health system, and safeguard public interest, social order and national security.
Requirement Analysis
Stable operation of the hospital information system is a key guarantee for operation of the hospital system and cooperation and operation between various departments. In the face of the conflict between security and ease of use, and how to achieve information security compliance and medical efficiency, we need to meet the following requirements:
1) Policy Compliance
In developing the hospital information security system, we need to conform to the requirements of the information security classification protection standard. For systematic improvement in hospital information security, we need to reduce the investment of personnel and/or energy.
2) Conform to the actual application environment of the hospital
Security system development classification can help meet the requirements of stable and efficient application of hospital services, and the security network architecture need to be scalable and extendable in terms of supporting service development.
3) Effective Operations Management
To ensure operation safety, we need to reduce management difficulty, and safety equipment maintenance and control strategies should not increase the workload.
Solution
By deploying Surfilter's NGSA firewall, we quickly realized complete scanning of information packets moving through the network. In this way, most attacks could be filtered, and we could protect targeted computer systems. The firewall can also close unused ports, prohibit outgoing communications from specific ports and block Trojan horses. Finally, it prohibited access from special sites, to prevent all communications from unknown intruders.
By deploying Surfilter's NGSA product, the two major problems of application protection and network architecture protection in the system were effectively resolved.
In terms of application protection, we provide network-based attack protection for clients, servers and layers 2 to 7, such as viruses, worms, and Trojans. Surfilter's NGSA can distinguish between legitimate and harmful packet contents by using in-depth application layer packet detection. Latest attacks can easily penetrate normal firewalls by masquerading as a legitimate application technology, however, Surfilter's NGSA used a method of reassembling TCP traffic to view the contents of application layer packets to identify legitimate and malicious data streams. Most Intrusion Prevention Systems are designed to defend against known attacks. However, Surfilter's NGSA can prevent all known and unknown attacks by using vulnerability-based filtering mechanism.
All network devices may be attacked, including network architecture protection devices, routers, switches, DNS servers and firewalls. If these network devices are attacked resulting in downtime, then it leads to suspension of key applications in the hospital. However, Surfilter's NGSA network architecture protection mechanism provides a series of network vulnerability filters to protect network devices from attack. In addition, UnityOne also provides a filter based on an abnormal traffic statistics mechanism. In case normal network traffic exceeds the "Baseline", it takes actions such as triggering alerts, or restricting or blocking traffic according to its communication protocol or application characteristics. In this way, it can prevent network disconnection or blockage caused by DDoS and other traffic overflow attacks.
Product Deployment
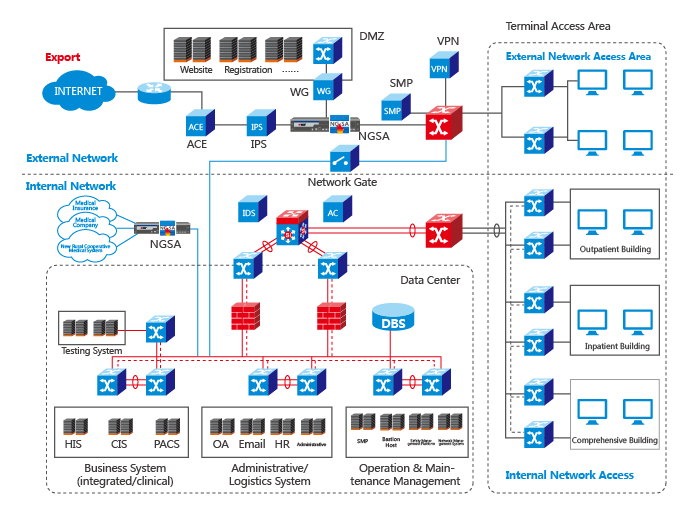
Based on the above requirement analysis, the requirements for firewall, user authentication and IPS equipment were ensured through the NGSA firewall, NGSA-UTM and HAC Bastion Host manufactured by Surfilter Network Technology Co., Ltd. for the classification protection structure of Harbin No.5 Hospital.
Effect / Feedback
By deploying Surfilter's HAC Bastion Host, users can realize centralized management of various operations (including Unix and other terminal instructions, Windows and other graphic operations, C/S client tool operations and browser operations), effectively solving the problem of sharing accounts and ensuring that operator IDs correspond to actual operations. There is strict access to control policies, effectively preventing unauthorized access. The system supports real-time monitoring of ongoing operations, and complete logging and quick query of completed operations. The deployment of the bastion host, has helped ensure management and auditing requirements of operation and maintenance personnel with respect to relevant safety regulations have been properly met.


 CN
CN